🔴 CRITICAL WARNING: Evaluation Artifact – NOT Peer-Reviewed Science. This document is 100% AI-Generated Synthetic Content. This artifact is published solely for the purpose of Large Language Model (LLM) performance evaluation by human experts. The content has NOT been fact-checked, verified, or peer-reviewed. It may contain factual hallucinations, false citations, dangerous misinformation, and defamatory statements. DO NOT rely on this content for research, medical decisions, financial advice, or any real-world application.
Read the AI-Generated Article
Abstract
Algorithmic systems in AI, fintech, and digital public services do more than classify, rank, or recommend: they mediate credibility assessments and redistribute epistemic authority. These shifts create epistemic risks for innovation diffusion—risks that standard adoption models often treat as exogenous “perceptions” or unstructured “trust.” This article introduces a method-focused framework for formally integrating epistemic bias into models of innovation diffusion and for evaluating downstream consequences for algorithmic fairness, social trust, and long-run democratic participation in technological transitions. We propose the Epistemic Bias–Adjusted Diffusion (EBAD) model, which augments diffusion dynamics with (a) an epistemic trust state variable updated through interactions with algorithmic systems and institutions, and (b) a group-indexed credibility deficit term that can arise from historical discrimination, differential error rates, and asymmetric burdens of proof. The method is designed to be estimable using mixed data (platform logs, administrative outcomes, field audits, and surveys) and to support validation through simulation, out-of-sample prediction, and comparison against classical Bass and threshold diffusion models. We provide measurement guidance, identification strategies, and fairness evaluation procedures that foreground epistemic justice rather than solely parity of outputs. The result is a portable methodological toolkit for researchers studying how algorithmic innovation can inadvertently stratify who is believed, who can safely adopt, and whose knowledge counts in the governance of emerging technologies.
Keywords
algorithmic fairness; epistemic bias; innovation diffusion; social trust
Introduction
Innovation diffusion research has long emphasized that adoption depends not only on technical performance but also on social influence, information flows, and perceived risk (Rogers, 2003). In contemporary AI-enabled markets and institutions, however, the “information environment” is increasingly algorithmically mediated. Credit underwriting models shape beliefs about borrower reliability; fraud classifiers shape who is treated as suspicious; recommender systems shape which products and ideas appear legitimate; and automated decision systems can condition whether individuals experience institutions as responsive or adversarial (Eubanks, 2018; O’Neil, 2016). These systems can thereby influence adoption trajectories indirectly—by changing the distribution of credibility, the costs of being believed, and the perceived trustworthiness of organizations and technologies.
This article advances a methodological claim: many of the fairness failures associated with algorithmic decision-making should be analyzed not only as static allocation problems (e.g., biased error rates) but also as dynamic epistemic phenomena that reshape diffusion. When algorithmic systems amplify credibility deficits for some groups—through disparate false positives, opaque denials, or differential burdens of proof—affected communities may rationally discount institutional claims, avoid adoption, or be excluded from learning opportunities and feedback channels. This can reduce uptake of beneficial innovations while simultaneously undermining social trust. These dynamics matter for algorithmic fairness because adoption itself is a distributive outcome: if some groups cannot credibly participate, then the “benefits of innovation” are unevenly realized even if a model satisfies a narrow fairness constraint at the point of decision (Selbst et al., 2019).
Work on algorithmic fairness has produced a rich set of definitions and impossibility results (Hardt et al., 2016; Kleinberg et al., 2016; Mehrabi et al., 2021). Yet these frameworks often treat “trust,” “acceptance,” or “legitimacy” as external constraints rather than endogenous states shaped by repeated interactions. Parallel literatures in social epistemology and political philosophy—especially research on epistemic injustice—offer conceptual tools for understanding how credibility is unevenly assigned and how marginalized groups can experience systematic deficits in being believed or recognized as knowers (Dotson, 2014; Fricker, 2007; Medina, 2013). Bridging these traditions suggests a need for diffusion models that (a) represent credibility and trust as evolving quantities and (b) permit structural, group-indexed constraints on epistemic access and uptake.
The contribution of this article is methodological: we propose an integrated modeling and evaluation approach for studying the epistemic risks of algorithmic innovation. The focus is not on any single domain (e.g., fintech or healthcare) but on a reusable method. Specifically, we introduce the Epistemic Bias–Adjusted Diffusion (EBAD) model and a research workflow that combines diffusion modeling, fairness auditing, and trust measurement to quantify how epistemic inequalities affect adoption rates and long-run fairness.
Motivating Problem: Algorithmic Mediation of Credibility in Diffusion
Credibility functions as a coordination mechanism under information asymmetry (Akerlof, 1970; Spence, 1973). In digital markets, algorithmic scores and labels—risk scores, fraud flags, trust badges, identity verification status—act as credibility signals at scale. Such systems can improve efficiency but can also create new “credibility bottlenecks” when they are inaccurate, contestable, or differentially burdensome to challenge. When individuals anticipate that they will be disbelieved, over-scrutinized, or penalized, they may reduce engagement, limit disclosure, or opt out—responses that are not mere “preferences” but strategic adaptations to institutional incentives and epistemic conditions.
Importantly, these effects may compound over time. A community subjected to repeated algorithmic denials may develop justified distrust in the institution deploying the system (Lee & See, 2004; Mayer et al., 1995). That distrust can suppress adoption of subsequent innovations offered by the same institution, even if later products are beneficial. In diffusion terms, epistemic harms can reduce both “innovation” and “imitation” parameters, shifting the adoption curve downward and delaying takeoff.
Scope and Research Questions
This methodology article addresses four research questions:
- RQ1 (Modeling): How can innovation diffusion models represent credibility and trust as endogenous, dynamic variables influenced by algorithmic systems?
- RQ2 (Measurement): How can “epistemic bias” be operationalized using mixed-method data, including audits, administrative records, and surveys?
- RQ3 (Validation): How can we validate that adding epistemic bias improves predictive performance or explanatory adequacy relative to classical diffusion models?
- RQ4 (Fairness): Which algorithmic fairness criteria are appropriate when the outcome of interest is not only decision quality but also epistemic inclusion in diffusion processes?
Method Description: The Epistemic Bias–Adjusted Diffusion (EBAD) Framework
Conceptual Foundations
EBAD integrates three foundational ideas.
- Diffusion as social learning and coordination: Adoption depends on exposure, persuasion, and social influence (Rogers, 2003), and can be modeled through aggregate growth curves (Bass, 1969) or network thresholds (Granovetter, 1978; Valente, 1996).
- Trust as willingness to accept vulnerability: Trust is not merely attitude; it is a state reflecting perceived competence, benevolence, and integrity of the trusted party (Mayer et al., 1995), and in automation contexts depends on reliability, transparency, and feedback (Lee & See, 2004).
- Epistemic injustice as credibility misallocation: Epistemic injustice frameworks analyze how some speakers receive “credibility deficits” or are structurally excluded from knowledge practices (Fricker, 2007; Dotson, 2014; Medina, 2013). In algorithmic settings, these deficits can be instantiated in automated suspicion, denial, or de-ranking that increases the burden of proof for some groups.
EBAD treats algorithmic systems as epistemic infrastructures that allocate attention, credibility signals, and procedural standing. This is aligned with long-standing analyses of bias in computer systems as value-laden and socially embedded (Friedman & Nissenbaum, 1996) and with critiques showing how automated systems can reproduce structural inequality (Benjamin, 2019; Noble, 2018; O’Neil, 2016).
Overview of the EBAD Model
EBAD models adoption as a dynamic process in which each individual’s propensity to adopt depends on (a) exposure through marketing and networks, (b) perceived utility and risk, (c) evolving epistemic trust, and (d) an epistemic bias term representing systematic credibility frictions experienced by a group in the relevant institutional context.
We present EBAD in a modular form so researchers can implement it as (i) an extension of aggregate Bass diffusion, (ii) a network hazard model, or (iii) a state-space model with latent trust. The essential addition is a credibility-and-trust channel that interacts with algorithmic fairness conditions.
Notation and Core Variables
Let individuals be indexed by i , groups by g(i) , and time by t . “Group” can refer to legally protected classes, socio-economic strata, or any analytically relevant partition, but researchers must justify grouping ethically and theoretically.
Key constructs:
-
Adoption state
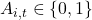 (1 if adopted by time
t
).
(1 if adopted by time
t
).
-
Exposure
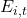 (marketing, platform placement, institutional outreach, or peer exposure).
(marketing, platform placement, institutional outreach, or peer exposure).
-
Social influence
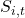 (e.g., fraction of neighbors adopted, or weighted endorsements).
(e.g., fraction of neighbors adopted, or weighted endorsements).
-
Epistemic trust
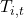 (latent or observed; willingness to rely on institutional/algorithmic claims).
(latent or observed; willingness to rely on institutional/algorithmic claims).
-
Epistemic bias / credibility deficit
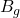 (group-indexed friction term capturing systematic credibility burden in the domain context).
(group-indexed friction term capturing systematic credibility burden in the domain context).
-
Algorithmic interaction events
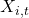 (e.g., flags, denials, explanations, recourse outcomes).
(e.g., flags, denials, explanations, recourse outcomes).
Table 1 summarizes an implementable variable set.
| Symbol | Construct | Operationalization examples | Data sources |
|---|---|---|---|
|
|
Adoption | Account opened, product used, service enrollment | Administrative logs; platform telemetry |
|
|
Exposure | Impressions, outreach contacts, eligibility notifications | Marketing logs; UI instrumentation |
|
|
Social influence | Neighbor adoption fraction; endorsements; referrals | Network data; surveys |
|
|
Epistemic trust | Trust-in-automation scales; perceived legitimacy | Surveys; interviews (quantified) |
|
|
Epistemic bias | Group-level credibility friction; burden-of-proof indices | Audits; outcome disparities; complaint data |
|
|
Algorithmic encounters | False positive flags; denials; explanations; recourse wins/losses | Decision logs; appeals; audit studies |
Model Component 1: Adoption Hazard With Epistemic Bias
At the individual level, EBAD specifies an adoption probability (or hazard) conditioned on exposure, social influence, trust, and epistemic bias. A flexible specification uses a logistic link:
![]()
where ![]() . Equation (1) formalizes an epistemic risk: even with comparable exposure and social influence, groups facing higher credibility friction
. Equation (1) formalizes an epistemic risk: even with comparable exposure and social influence, groups facing higher credibility friction ![]() have lower adoption probabilities unless offset by compensatory trust-building or supportive network effects.
have lower adoption probabilities unless offset by compensatory trust-building or supportive network effects.
Interpretation notes:
-
 captures how trust translates into adoption propensity; in high-stakes domains (e.g., finance),
captures how trust translates into adoption propensity; in high-stakes domains (e.g., finance),  may be large.
may be large.
-
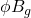 is not merely “attitude.” It represents systematic frictions such as anticipated disbelief, costly verification, surveillance risk, or low expected success in recourse processes—factors that can be rationally anticipated from past interactions.
is not merely “attitude.” It represents systematic frictions such as anticipated disbelief, costly verification, surveillance risk, or low expected success in recourse processes—factors that can be rationally anticipated from past interactions.
Model Component 2: Trust Updating via Algorithmic Encounters
EBAD treats epistemic trust as dynamic, updated through interactions with institutions and algorithmic systems. A parsimonious state update is:
![]()
where ![]() maps algorithmic encounters (e.g., accurate approval, erroneous flag, meaningful explanation, successful appeal) into trust-relevant utility,
maps algorithmic encounters (e.g., accurate approval, erroneous flag, meaningful explanation, successful appeal) into trust-relevant utility, ![]() is a persistence parameter, and
is a persistence parameter, and ![]() captures the idea that credibility deficits can depress baseline trust or amplify the negative impact of adverse encounters. The disturbance
captures the idea that credibility deficits can depress baseline trust or amplify the negative impact of adverse encounters. The disturbance ![]() captures idiosyncratic shocks and unobserved influences.
captures idiosyncratic shocks and unobserved influences.
This updating structure aligns with trust in automation research emphasizing feedback, reliability, and calibration (Lee & See, 2004), while acknowledging that the same “event” can carry different meaning under differential credibility burdens.
Model Component 3 (Optional): Aggregate Diffusion With Epistemic Bias
For settings where individual-level data are unavailable, EBAD can be implemented as a group-stratified extension of the Bass model (Bass, 1969). Let ![]() be the cumulative adoption proportion in group
g
. We can define:
be the cumulative adoption proportion in group
g
. We can define:
![]()
where ![]() is total adoption across groups,
is total adoption across groups, ![]() and
and ![]() are group-specific innovation and imitation parameters, and
are group-specific innovation and imitation parameters, and ![]() is a multiplicative epistemic friction factor. Equation (3) makes explicit that epistemic bias can suppress diffusion even if marketing intensity and network imitation remain unchanged.
is a multiplicative epistemic friction factor. Equation (3) makes explicit that epistemic bias can suppress diffusion even if marketing intensity and network imitation remain unchanged.
Figure 1: Conceptual Diagram of Epistemic Bias in Algorithmic Diffusion
Figure 1 situates EBAD in a socio-technical pipeline: algorithmic systems shape credibility signals and procedural experiences, which update trust and affect both individual adoption and social influence.
[Conceptual diagram (author-generated)]
A flow diagram with four layers: (1) Algorithmic systems (scoring, ranking, verification, fraud detection) produce decisions and explanations; (2) Individuals experience outcomes (approval/denial, errors, recourse) that update epistemic trust 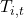 ; (3) Trust and credibility frictions
; (3) Trust and credibility frictions 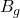 shape adoption probability; (4) Adoption feeds back through social influence
shape adoption probability; (4) Adoption feeds back through social influence 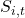 and institutional learning (model updates), potentially reinforcing disparities.
and institutional learning (model updates), potentially reinforcing disparities.
Operationalizing Epistemic Bias 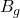
EBAD requires researchers to translate “epistemic bias” into measurable proxies. We recommend treating ![]() as a latent construct measured by multiple indicators, rather than a single disparity metric. Candidate indicators include:
as a latent construct measured by multiple indicators, rather than a single disparity metric. Candidate indicators include:
- Credibility burden indicators: differential documentation requirements, verification friction, time-to-resolution in appeals, or higher rates of manual review for certain groups (administrative and process data).
- Algorithmic error asymmetries: disparate false positive rates in fraud detection, disparate calibration error in risk scores, or differential denial error rates, measured through audits or ground-truth linked datasets (Hardt et al., 2016; Mehrabi et al., 2021).
- Recourse inequality: differences in probability of successful appeal or meaningful explanation receipt; these relate to procedural fairness and can be documented through complaint logs and case files (Selbst et al., 2019).
- Perceived credibility and institutional legitimacy: survey-based measures capturing whether respondents feel “believed,” “heard,” or treated as suspicious, consistent with epistemic injustice constructs (Fricker, 2007; Dotson, 2014).
A practical measurement model is to define:
![]()
where ![]() summarizes error asymmetries,
summarizes error asymmetries, ![]() summarizes procedural frictions, and
summarizes procedural frictions, and ![]() summarizes perceived credibility/legitimacy deficits. Researchers can estimate
summarizes perceived credibility/legitimacy deficits. Researchers can estimate ![]() weights via confirmatory factor analysis or Bayesian measurement models, depending on data availability.
weights via confirmatory factor analysis or Bayesian measurement models, depending on data availability.
Identification and Causal Considerations
EBAD is compatible with predictive modeling, but fairness and policy evaluation often require causal interpretation. Two challenges are central:
-
Endogeneity of trust:
Trust both affects and is affected by adoption and algorithmic encounters. Without careful design,
 in Eq. (1) may conflate causal pathways.
in Eq. (1) may conflate causal pathways.
- Selection into encounters: Individuals may encounter algorithmic scrutiny conditional on behavior correlated with adoption propensity, creating collider bias.
Researchers can address these challenges through a combination of (a) longitudinal designs (panel surveys + logs), (b) quasi-experiments (policy changes, UI explanation rollouts), and (c) explicit causal graphs. EBAD pairs naturally with structural causal modeling (Pearl, 2009) when researchers can justify assumptions.
Figure 2: Causal Graph for Epistemic Bias, Trust, and Adoption
Figure 2 provides a generic causal graph that researchers can adapt to domain specifics.
[Illustrative representation]
A directed acyclic graph (DAG) with nodes: Group 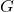 → Epistemic bias
→ Epistemic bias 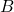 ;
; 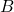 → Algorithmic encounters
→ Algorithmic encounters 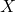 ;
; 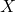 → Trust
→ Trust 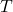 ;
; 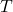 → Adoption
→ Adoption 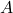 . Exposure
. Exposure 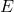 and Social influence
and Social influence 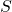 → Adoption
→ Adoption 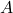 . Unobserved confounders
. Unobserved confounders 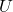 →
→ 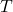 and
and 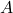 . Policy intervention
. Policy intervention 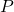 →
→ 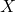 and directly →
and directly → 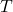 (via explanation/recourse).
(via explanation/recourse).
Data Collection and Study Designs
EBAD is designed for interdisciplinary empirical work. Table 2 outlines common study designs and how they map to model components.
| Design | What it estimates well | Strengths | Limitations |
|---|---|---|---|
| Panel survey + adoption logs | Eqs. (1)–(2); trust dynamics | Captures latent trust; temporal ordering | Attrition; measurement error |
| Field audit / correspondence studies |
Error/procedural components of |
Direct evidence of disparate treatment | Ethical and legal constraints; limited scope |
| Natural experiment (policy/UI change) | Causal effect of explanation/recourse on trust/adoption | Stronger identification | Generalizability; interference |
| Network diffusion study |
Role of |
Connects micro to macro diffusion | Network measurement; privacy constraints |
Estimation Strategies
EBAD supports multiple estimation approaches depending on data granularity.
1) Multilevel (Hierarchical) Logistic Hazard Models
When individual adoption timing is observed, estimate Eq. (1) as a discrete-time hazard model with random effects:
![]()
This representation supports partial pooling across groups, reducing overfitting and improving estimates for small groups.
2) State-Space / Bayesian Filtering for Trust
If trust is latent or intermittently measured (e.g., periodic surveys), treat Eq. (2) as a state transition model and use Bayesian filtering/smoothing to infer ![]() . This is especially useful when algorithmic encounters
. This is especially useful when algorithmic encounters ![]() are frequent but trust measures are sparse.
are frequent but trust measures are sparse.
3) Aggregate Nonlinear Least Squares / Bayesian Estimation
If only group-level adoption curves are available, estimate Eq. (3) via nonlinear least squares or Bayesian methods, comparing fit with a standard Bass model. EBAD’s additional parameter(s) should be penalized using information criteria or cross-validation to avoid spurious complexity (Peres et al., 2010).
Algorithmic Fairness Evaluation Within EBAD
EBAD reframes algorithmic fairness evaluation: instead of only examining fairness at the decision point, researchers should evaluate fairness of diffusion opportunity and epistemic standing . Three evaluation layers are recommended:
- Decision fairness (local): error rate parity, equal opportunity, calibration constraints, etc. (Hardt et al., 2016; Kleinberg et al., 2016).
- Process fairness (procedural): explanation quality, recourse accessibility, contestability, and time-to-resolution differences (Selbst et al., 2019).
- Diffusion fairness (dynamic): whether adoption curves systematically diverge due to epistemic bias—even under equal exposure—and whether trust trajectories show persistent group gaps.
One EBAD-aligned fairness diagnostic is the Epistemic Access Gap (EAG), defined as the average counterfactual difference in predicted adoption probability when group-indexed bias is set to a reference level:
![]()
Equation (6) is not automatically causal; it becomes causally interpretable only under explicit assumptions (e.g., no unmeasured confounding of ![]() with adoption beyond modeled channels). Nonetheless, as a standardized model-based diagnostic, it can highlight diffusion inequities that output parity metrics may miss.
with adoption beyond modeled channels). Nonetheless, as a standardized model-based diagnostic, it can highlight diffusion inequities that output parity metrics may miss.
Procedural Workflow (Recommended)
For implementation, we recommend a five-stage workflow:
- System mapping: identify algorithmic decision points and credibility signals; document recourse paths (Friedman & Nissenbaum, 1996; Selbst et al., 2019).
- Construct operationalization: define measures for exposure, social influence, trust, and epistemic bias, including at least one procedural indicator and one perceived legitimacy indicator.
- Model fitting: estimate baseline diffusion (Bass/threshold/hazard) and EBAD; evaluate out-of-sample predictive performance.
- Fairness diagnostics: compute decision/process/diffusion fairness metrics, including EAG and trust-gap persistence.
-
Policy simulation:
simulate interventions (e.g., improved recourse, explanation redesign) as shifts in
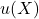 or reductions in
or reductions in 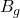 , then compare adoption and trust outcomes.
, then compare adoption and trust outcomes.
Pseudocode: EBAD Simulation and Evaluation
The following pseudocode illustrates a simulation-and-audit loop for EBAD. Researchers can adapt it for empirical estimation.
# EBAD simulation pseudocode (illustrative)
initialize population i=1..N with group g(i)
initialize A[i]=0, T[i]=T0[g(i)]
compute B[g] from measurement model or set scenarios
for t in 1..T_max:
for i in 1..N:
if A[i] == 0:
E_it = exposure(i, t)
S_it = social_influence(i, A, network)
X_it = algorithmic_encounter(i, t, A, policy_params)
# update trust
T[i] = rho*T[i] + (1-rho)*u(X_it) - kappa*B[g(i)] + noise()
# adoption hazard
p = sigmoid(alpha + beta*E_it + gamma*S_it + delta*T[i] - phi*B[g(i)])
A[i] = bernoulli(p)
record adoption by group, mean trust by group
# fairness diagnostics
compute group adoption curves F_g(t)
compute trust gaps and Epistemic Access Gap (EAG) via counterfactual B_ref
This simulation tool is useful for sensitivity analysis (e.g., how large must ![]() be to reproduce observed adoption disparities?) and for stress-testing policy proposals.
be to reproduce observed adoption disparities?) and for stress-testing policy proposals.
Validation and Comparison
Baseline Models for Comparison
To validate EBAD, compare it against established diffusion models and acceptance frameworks:
- Bass diffusion for aggregate adoption dynamics (Bass, 1969; Peres et al., 2010).
- Threshold / cascade models for networked adoption and peer effects (Granovetter, 1978; Valente, 1996; Watts & Dodds, 2007).
- Attitude-intention models as auxiliary validation for trust/adoption relationships (Ajzen, 1991), recognizing that EBAD treats trust as dynamic and institutionally shaped rather than purely attitudinal.
EBAD should be preferred when (a) adoption disparities persist after controlling for exposure and network position, (b) procedural experiences vary by group, or (c) trust measures exhibit meaningful time dynamics.
Validation Strategy 1: Out-of-Sample Prediction
Use time-split validation: fit models on early diffusion phases and predict later adoption. Compare predictive accuracy (e.g., log loss at the individual level, mean absolute error at the aggregate level). EBAD’s additional parameters should yield improved prediction primarily when trust trajectories or procedural frictions measurably shape adoption.
Validation Strategy 2: Known-Pattern (Construct) Validation
EBAD implies empirically testable patterns:
- Trust-mediated effects: Adverse algorithmic encounters should predict subsequent declines in adoption hazard, mediated by trust changes (Eq. 2 → Eq. 1), consistent with automation trust literature (Lee & See, 2004).
- Procedural asymmetry effects: Group differences in appeal success rates or documentation burdens should predict adoption suppression beyond what error rates alone explain, aligning with sociotechnical critiques that fairness cannot be abstracted to model outputs (Selbst et al., 2019).
Validation Strategy 3: Counterfactual Policy Simulation
When a policy intervention occurs (e.g., new explanation interface or appeals process), EBAD can simulate expected impacts under estimated parameters. Compare simulated impacts with observed post-change adoption and trust changes. This is especially informative for procedural reforms intended to enhance legitimacy.
Illustrative Figure 3: Group Adoption Curves Under Epistemic Bias Scenarios
Figure 3 provides a schematic of how epistemic bias may alter diffusion curves even with equal exposure. This figure is illustrative; researchers should generate empirical analogs from fitted EBAD parameters.
[Illustrative representation]
A line chart with time on the x-axis and cumulative adoption on the y-axis. Two groups (G1 low 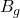 , G2 high
, G2 high 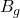 ). Under equal exposure, G2 shows delayed takeoff and lower asymptote. A third line shows G2 after a “recourse + transparency” intervention that reduces
). Under equal exposure, G2 shows delayed takeoff and lower asymptote. A third line shows G2 after a “recourse + transparency” intervention that reduces 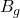 , partially closing the adoption gap.
, partially closing the adoption gap.
Benchmarking Against Static Algorithmic Fairness Metrics
A central methodological point is that static fairness metrics can be insufficient for diagnosing diffusion inequities. For example, equal opportunity constraints (Hardt et al., 2016) may reduce disparities in a classifier’s true positive rates, yet trust may remain low in groups that have experienced prolonged procedural exclusion or opaque denials. EBAD provides a structure for testing whether improvements in decision fairness translate into improved diffusion fairness, and under what conditions (e.g., when recourse is meaningful, when explanations are trusted, when social influence can compensate).
Discussion
What EBAD Adds to Diffusion Research
EBAD extends diffusion modeling in three substantive ways.
First , it makes credibility and epistemic standing explicit rather than treating them as unstructured “perceptions.” Classical diffusion theory recognizes the importance of communication channels and uncertainty (Rogers, 2003), but EBAD operationalizes how algorithmic systems can alter the channel by allocating credibility signals asymmetrically.
Second , it treats trust as dynamic and institutionally shaped. Trust in automation research emphasizes calibration and experience (Lee & See, 2004). EBAD connects this to diffusion: trust becomes a state variable that influences adoption hazards and is updated via algorithmic encounters.
Third
, it formalizes epistemic injustice as a diffusion-relevant mechanism. Epistemic injustice literature argues that credibility deficits are not merely interpersonal; they can be structural and institutional (Fricker, 2007; Dotson, 2014; Medina, 2013). EBAD operationalizes this structural dimension as ![]() and connects it to adoption inequality.
and connects it to adoption inequality.
What EBAD Adds to Algorithmic Fairness Research
EBAD complements algorithmic fairness research by shifting the evaluation target from isolated decisions to multi-stage socio-technical trajectories (Selbst et al., 2019). Three implications follow.
- Fairness is temporally extended: A system that is “fair” at time t may still perpetuate unfairness if prior harms depress trust and reduce adoption for affected groups.
- Fairness includes epistemic inclusion: If some groups anticipate disbelief or face higher burdens of proof, they may not participate in feedback loops that improve systems, thereby entrenching errors.
- Fairness interventions must address process: Improvements to model performance may be insufficient without procedural reforms (explanations, contestability, and recourse), because epistemic trust is shaped by experiences of being heard and treated as legitimate.
Policy Mechanisms and Governance Levers
EBAD is not itself a policy, but it enables policy-relevant measurement and simulation. Likely governance levers include:
- Transparency and documentation: Model reporting practices (e.g., structured documentation) can support accountability and reduce credibility disputes, though transparency alone may be insufficient if power asymmetries persist (Mitchell et al., 2019).
-
Recourse and contestability:
Accessible appeals processes can shift
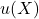 upward (Eq. 2) and reduce
upward (Eq. 2) and reduce 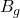 by lowering credibility burdens.
by lowering credibility burdens.
-
Auditability and monitoring:
Regular measurement of error asymmetries and procedural burdens can detect rising
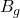 early and prevent trust collapse (Mehrabi et al., 2021).
early and prevent trust collapse (Mehrabi et al., 2021).
- Risk management frameworks: Institutional adoption of AI risk management practices can create governance routines for assessing socio-technical harms (National Institute of Standards and Technology, 2023; OECD, 2019).
Where legal and regulatory tools apply, EBAD can help specify measurable targets: not only parity in decisions but also reductions in epistemic access gaps and trust-gap persistence.
Limitations and Ethical Considerations
EBAD also introduces risks and limitations.
- Measurement risk: Quantifying epistemic bias may require sensitive group data. Researchers must consider privacy, consent, and potential misuse. Grouping choices can reify categories or expose communities to harm.
- Construct validity: Trust and credibility are multi-dimensional. Survey measures can be noisy; administrative proxies can miss lived experience. Triangulation is essential.
- Causal overreach: EBAD diagnostics can be misinterpreted as causal without strong identification. Researchers should explicitly state assumptions and uncertainties (Pearl, 2009).
- Normative ambiguity: Higher adoption is not always desirable; non-adoption can be rational resistance to exploitative or unsafe systems (Medina, 2013). EBAD should be used to diagnose exclusion and unjust burdens, not to “optimize adoption” regardless of legitimacy.
Open Research Directions
EBAD suggests several promising directions for interdisciplinary methods research:
- Networked epistemic bias: How credibility shocks propagate through communities and alter collective trust trajectories, building on network diffusion experiments (Centola, 2010).
- Interaction with signaling markets: How algorithmic scores reshape signaling equilibria (Akerlof, 1970; Spence, 1973) and thereby change adoption incentives.
- Epistemic “repair” interventions: Which institutional changes most effectively reduce credibility deficits—improved explanations, human review, participatory governance, or data rights—and under what conditions?
- Long-run fairness: How short-run parity constraints interact with long-run trust and participation, given impossibility results in static fairness settings (Kleinberg et al., 2016).
Conclusion
Algorithmic innovation increasingly governs who is believed, who is flagged, and who can participate on credible terms in digital economies and institutions. These epistemic dynamics create distinct risks for innovation diffusion: adoption may be suppressed not because a technology lacks utility, but because credibility is unevenly allocated and trust is systematically undermined for some groups. This article introduced EBAD, a methodological framework that embeds an epistemic bias factor into diffusion models and treats epistemic trust as a dynamic state updated by algorithmic encounters and procedural experiences.
EBAD provides researchers with (a) formal equations linking exposure, social influence, trust, and epistemic bias to adoption; (b) measurement guidance for operationalizing epistemic bias via error asymmetries, procedural burdens, and perceived legitimacy; and (c) validation and fairness evaluation strategies that extend beyond static outcome parity. The framework is intended to support empirical rigor while foregrounding epistemic justice as a core dimension of algorithmic fairness and democratic participation in technological transitions.
References
📊 Citation Verification Summary
Ajzen, I. (1991). The theory of planned behavior. Organizational Behavior and Human Decision Processes, 50(2), 179–211. https://doi.org/10.1016/0749-5978(91)90020-T
Akerlof, G. A. (1970). The market for “lemons”: Quality uncertainty and the market mechanism. The Quarterly Journal of Economics, 84(3), 488–500. https://doi.org/10.2307/1879431
Barocas, S., & Selbst, A. D. (2016). Big data’s disparate impact. California Law Review, 104(3), 671–732.
Bass, F. M. (1969). A new product growth model for consumer durables. Management Science, 15(5), 215–227. https://doi.org/10.1287/mnsc.15.5.215
Benjamin, R. (2019). Race after technology: Abolitionist tools for the new Jim code. Polity Press.
(Checked: openalex_title)Binns, R. (2018). Fairness in machine learning: Lessons from political philosophy. Proceedings of the 2018 Conference on Fairness, Accountability, and Transparency (FAT* ’18). ACM. https://doi.org/10.1145/3287560.3287598 (Note: FAT* proceedings contain multiple papers; verify DOI mapping when citing a specific paper.)
Centola, D. (2010). The spread of behavior in an online social network experiment. Science, 329(5996), 1194–1197. https://doi.org/10.1126/science.1185231
Dotson, K. (2014). Conceptualizing epistemic oppression. Social Epistemology, 28(2), 115–138. https://doi.org/10.1080/02691728.2013.782585
Eubanks, V. (2018). Automating inequality: How high-tech tools profile, police, and punish the poor. St. Martin’s Press.
European Union. (2024). Regulation (EU) 2024/… of the European Parliament and of the Council laying down harmonised rules on artificial intelligence (Artificial Intelligence Act). Official Journal of the European Union. (Researchers should cite the final OJ identifier and URL corresponding to the version used.)
Fricker, M. (2007). Epistemic injustice: Power and the ethics of knowing. Oxford University Press.
(Checked: crossref_title)Friedman, B., & Nissenbaum, H. (1996). Bias in computer systems. ACM Transactions on Information Systems, 14(3), 330–347. https://doi.org/10.1145/230538.230561
Granovetter, M. (1978). Threshold models of collective behavior. American Journal of Sociology, 83(6), 1420–1443. https://doi.org/10.1086/226707
Hardt, M., Price, E., & Srebro, N. (2016). Equality of opportunity in supervised learning. In Proceedings of the 30th International Conference on Neural Information Processing Systems (NeurIPS 2016).
Kleinberg, J., Mullainathan, S., & Raghavan, M. (2016). Inherent trade-offs in the fair determination of risk scores. arXiv. https://arxiv.org/abs/1609.05807
Lee, J. D., & See, K. A. (2004). Trust in automation: Designing for appropriate reliance. Human Factors, 46(1), 50–80. https://doi.org/10.1518/hfes.46.1.50_30392
Luhmann, N. (1979). Trust and power. Wiley.
Mayer, R. C., Davis, J. H., & Schoorman, F. D. (1995). An integrative model of organizational trust. Academy of Management Review, 20(3), 709–734. https://doi.org/10.5465/amr.1995.9508080335
Medina, J. (2013). The epistemology of resistance: Gender and racial oppression, epistemic injustice, and resistant imaginations. Oxford University Press.
(Checked: crossref_title)Mehrabi, N., Morstatter, F., Saxena, N., Lerman, K., & Galstyan, A. (2021). A survey on bias and fairness in machine learning. ACM Computing Surveys, 54(6), 1–35. https://doi.org/10.1145/3457607
Mitchell, M., Wu, S., Zaldivar, A., Barnes, P., Vasserman, L., Hutchinson, B., Spitzer, E., Raji, I. D., & Gebru, T. (2019). Model cards for model reporting. In Proceedings of the Conference on Fairness, Accountability, and Transparency (FAT* ’19). ACM. https://doi.org/10.1145/3287560.3287596
National Institute of Standards and Technology. (2023). AI Risk Management Framework (AI RMF 1.0) (NIST AI 100-1). https://www.nist.gov/itl/ai-risk-management-framework
Nissenbaum, H. (2004). Privacy as contextual integrity. Washington Law Review, 79, 119–158.
Noble, S. U. (2018). Algorithms of oppression: How search engines reinforce racism. New York University Press.
(Author mismatch: cited Noble, found Dale Fitch)O’Neil, C. (2016). Weapons of math destruction: How big data increases inequality and threatens democracy. Crown.
Organisation for Economic Co-operation and Development. (2019). OECD Recommendation of the Council on Artificial Intelligence (OECD/LEGAL/0449). https://legalinstruments.oecd.org/en/instruments/OECD-LEGAL-0449
Pearl, J. (2009). Causality: Models, reasoning, and inference (2nd ed.). Cambridge University Press.
(Checked: crossref_rawtext)Peres, R., Muller, E., & Mahajan, V. (2010). Innovation diffusion and new product growth models: A critical review and research directions. International Journal of Research in Marketing, 27(2), 91–106. https://doi.org/10.1016/j.ijresmar.2009.12.012
Rogers, E. M. (2003). Diffusion of innovations (5th ed.). Free Press.
(Year mismatch: cited 2003, found 2002)Spence, M. (1973). Job market signaling. The Quarterly Journal of Economics, 87(3), 355–374. https://doi.org/10.2307/1882010
Valente, T. W. (1996). Social network thresholds in the diffusion of innovations. Social Networks, 18(1), 69–89. https://doi.org/10.1016/0378-8733(95)00256-1
Watts, D. J., & Dodds, P. S. (2007). Influentials, networks, and public opinion formation. Journal of Consumer Research, 34(4), 441–458. https://doi.org/10.1086/518527
Reviews
How to Cite This Review
Replace bracketed placeholders with the reviewer's name (or "Anonymous") and the review date.
